Network
Summary
Networking basics
Internet
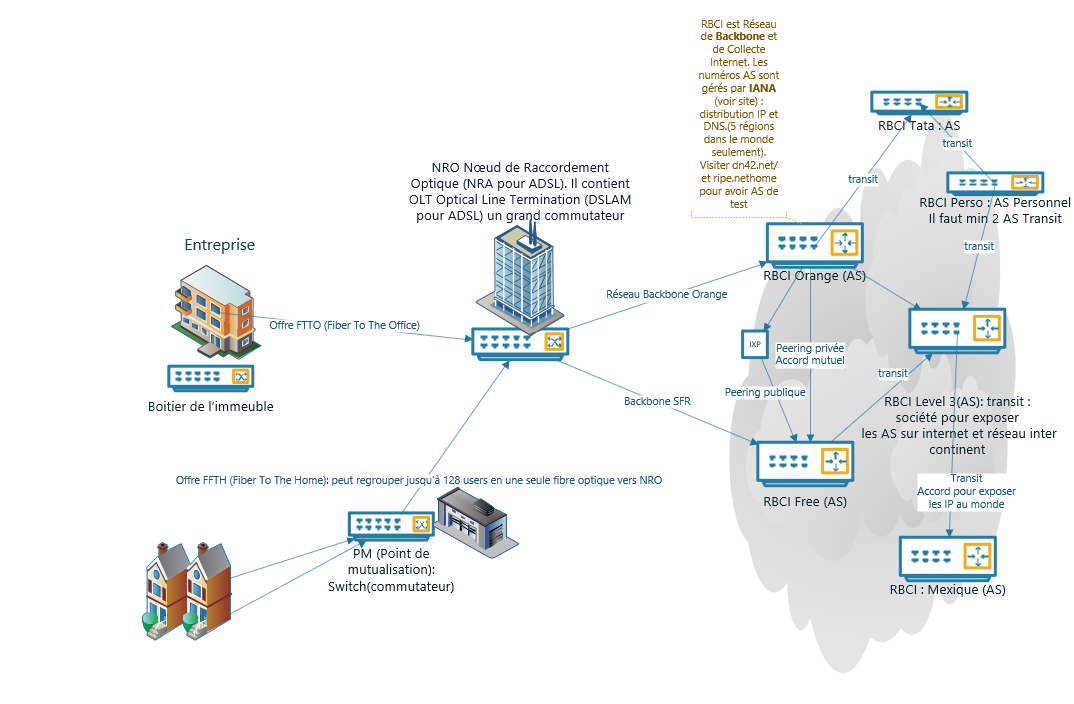
The network view of internet :
Backbon are big fiber cables between states or cities.
the peering can be between two AS and the numerci logictic can be low cost or in the same contry or between the AS
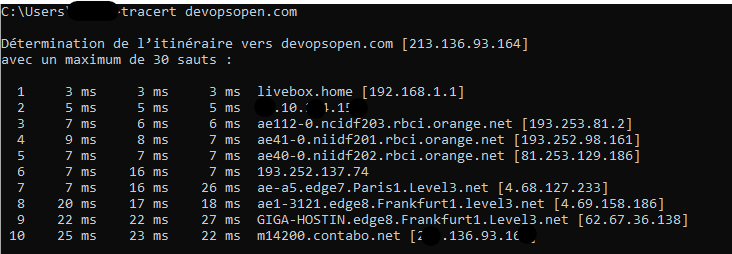
Example network paquets :
You can visit the site for more details :
https://www.arcep.fr/cartes-et-donnees/nos-publications-chiffrees/linterconnexion-de-donnees/barometre-de-linterconnexion-de-donnees-en-france.html : Autorité de régulation des communications électroniques, des postes et de la distribution de la presse give more information about internet
https://bgp.tools or https://bgp.he.net/ for informations about AS et IPs
https://www.iana.org/ IANA the subsidiary of ICANN who manage AS Numbers and IPs for AS, it manages also Domain name servers
https://dn42.net/home :to create a private network and simulate AS creation
https://blog.ataxya.net/un-as-chez-soi-cest-possible/ for more details of internet
https://tunnelbroker.net/ : site to get tunel for using IP6 free
https://academy.ripe.net/ : academy to be aware of creation AS and network, very important to begin with this web site
https://www.youtube.com/watch?v=X1QJphPLhlM : To visualiz NRO...
http://nsinfo.yo.fr/snt_internet_tcpip.html : Web site for OSI details and transmission of Data from A to B
Network bridge
Is a computer networking device that creates a single, aggregate network from multiple communication networks or network segments
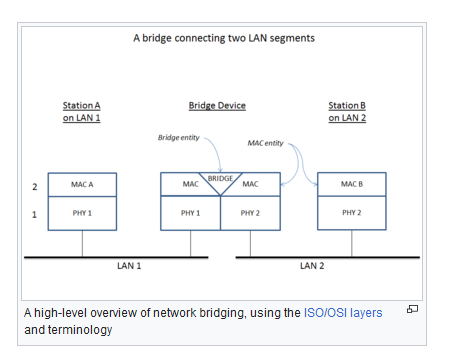
Network switch
Is a bridg but with multiport (also called switching hub, bridging hub, and, by the IEEE, MAC bridge[1]) is networking hardware that connects devices on a computer network by using packet switching to receive and forward data to the destination device.
A network switch is a multiport network bridge that uses MAC addresses to forward data at the data link layer (layer 2) of the OSI model. Some switches can also forward data at the network layer (layer 3) by additionally incorporating routing functionality. Such switches are commonly known as layer-3 switches or multilayer switches.[2]
To communicate with another device you can juste add the device with command :
ip addr add 192.168.1.10/24 dev eth0
Routing
For networking into the same network we can use switch but if you want to communicate with an extern network you use router
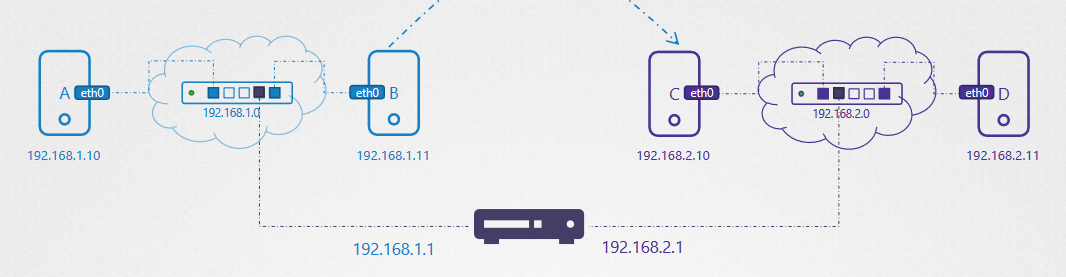
Gateway
If the network is a room the gateway is the door, as you can see into image above, the gatway is the adress ip 192.168.1.1
To see details of gatways , you can use command route and ip route add to add the gateway
route
ip route add 192.168.2.0/24 via 192.168.1.1
be attention of the sens of the flow, if the sens the flow is from the system C to system B so the command is bellow th add the ip into the iptable:
ip route add 192.168.1.0/24 via 192.168.2.1
we can also have a gateway for internet and add it to the iptable :
ip route add 172.217.194.0/24 via 192.168.2.1
We can also have a gateway for internet and add it to the iptable.
Take aways
ip link : is to list modifying interfaces in the host
ip addr : is to set ip adresses insignt into interfaces
ip addr add 192.168.1.10/24 dev eth0 : is to set ip adresse but is ephemere, if you want to persiste this change you should do it into the etc interface network file
ip route or route : is the see root table
ip route add 192.168.1.0/24 via 192.168.2.1 : is to add ip adresse into ip table
cat /proc/sys/net/ipv4/ip_forward : must equal 1 to check if ip forrwarding is active in the host
Dns
DNS is Domain Name System. To resolve a DNS, the schema bellow explaine the path of dns request without cache.
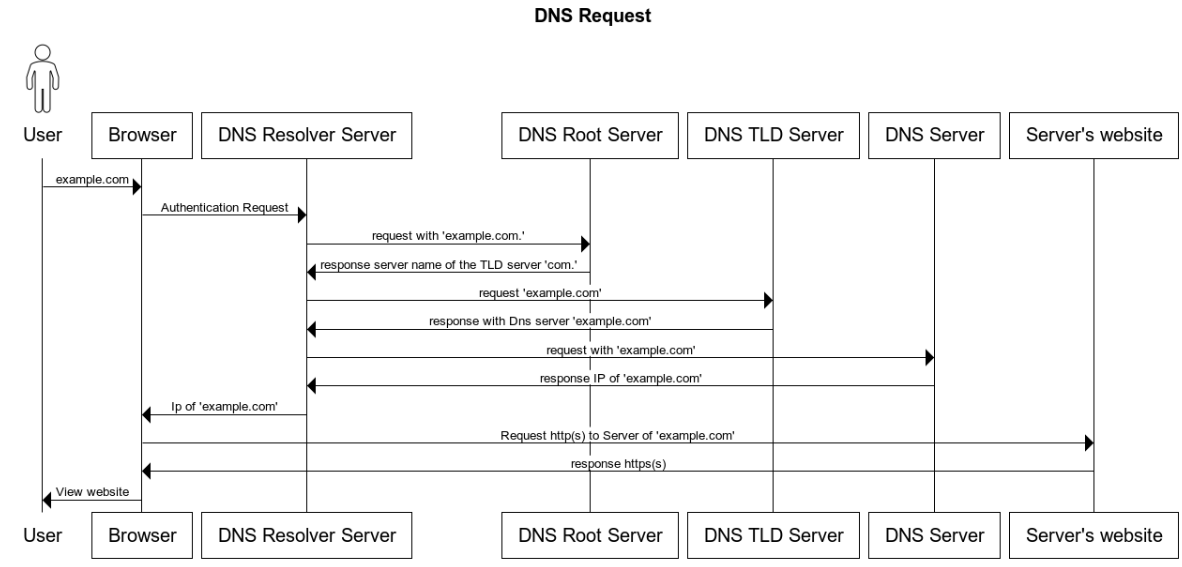
To communicate with other device you can add it in the host file
/etc/host
But commonly there is a server DNS, that you can configure it in Linux into the file
cat /etc/resolv.conf
nameserver 192.168.1.100
We can also chose the priority of the database that can be used to resolve dns with
cat /etc/nsswitch.confpasswd: files nis group: files nis hosts: files dns
'files' for local files, 'nis' for Network Information Service, 'nisplus' for NIS+, 'ldap' for protocole LDAP, or 'mysql' for MySQL database..
Sometimes there is no dns into the server and not into the host file so you can add ip dns server 8.8.8.8 (google dns server) to resolve it into 'resolv.conf' or add it into the dns server to forword request
Records stored into DNS server are:
A (Adresse record) web-server 192.168.1.2 : associate an IP4 adress to a Domain name system( A for ip4 adress)
AAAA (quad-Adress record) web-server AA25.215A.2354A.DA215 (AAAA for ip6 adress)
CNAME record (Canonical name record) : This DNS record operates as an alias. It specifies that a particular domain name is an a.b.a. for another domain name www.a.b.c
MX record (Mail exchange record) : This is a record that points to where your email is hosted. It's the record responsible for associating your domain name with an email server. And typically, one domain name can have more than one MX record
TXT record (text record) : TXT records are typically used for verification of a domain name, or implementing the Sender Policy Framework (SPF), and detecting forged use of domain names (for spam, phishing etc.)
SRV record (Server)
SN record (Name Server) :
You should know that when you request an URL, first we look for resolving the URI, so the request go to the DNS server to give us the ip adress . For example when you are at home, your livebox have a DNS server and it attribut to your machine and adresse IP of DNS server automaticaly "192.168.1.1" for example . When you want to access to a website, the request go to the DNS livebox server (if there is no resolving in you host file) and get the IP web site adress.
pour voir ses info sous Windows
Command for diag DNS :
nslookup google.com (the respons “Réponse ne faisant pas autorité” means that is came from the cach)
if you dont want to use the cache
nslookup -type=soa domain.com
for more details
nslookup -debug domain.com
dig google.com (command give more informations)
WAF and NF
WAF : Web Application Firewall protect applicayion web from web attacks like sql injection, DDOS, ... and is applyed on 7 layer OSI schema.
We use a WAF to filtre and monitor requests comming from internet to our system
NF : Network Firewall protect non web application from attacks of type SMTP, FTP ... and is applyed on the 3, 4 layer OSI.
So always we should have those two Firewall because it's complementary.
Reverse Proxy
A reverse proxy is a server in front of applications.
A reverse proxy can be used like a WAF (security), LB (perf and reliability), Global Server Load Balancing GSLB (Perf), Cache (perf), SSL Termination (Security), Routing
Load balancer
Load balancer is a compounent that dispatch trafic to many other compounent. There is several algorithms to load balance a trafic, you can see this website for more details :
https://kemptechnologies.com/load-balancer/load-balancing-algorithms-techniques
Network Namespaces
You can imagine a network namespace like a room in a home.
the home is the host and the namespace is the room, so to create a namespace network called red :
ip netns add red
in a node, you can see all interfaces with command link:
ip link
but if you want to execute this command in red namespace network :
ip netns exec red ip link or ip -n red link
the same thing with arp command to get resolution of MAc and IP
arp
into the network namespace
ip netns exec red arp
Connecting two namespaces blue and red nedd a vertual cable,
ip link add veth-red type veth peer name veth-blue
link the veth-red network to the namespace red and the veth-blue to blue namespace
ip link set veth-red netns redip link set veth-blue netns blue
Attribute an adress ip to the interface blue and red
ip -n red addr add 192.168.15.1 dev veth-redip -n blue addr add 192.168.15.2 dev veth-blue
ip -n red link set veth-red upip -n blue link set veth-blue up
test connection from red namspace to blue namespace
ip netns exec red ping 192.168.15.2
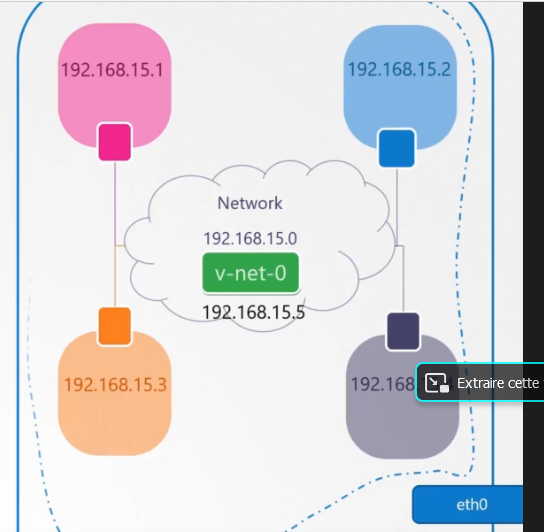
but if you have a lot of namspaces and you want to communicate them, you need a virtual switch like the virtual interface of the namespace.
There is a lot of solution like Linux bridge or open vSwitch. We use Linux Bridg
ip link add v-net-0 type bridge
with the command ip link, you can see the v-net-0 into the host but down so you can use the command 'ip link set dev v-net-0 up'
To connect the red interface to the vswitch, you need to delete the connection with the blue interface, so you can use the command :
ip -n red link del veth-red
create bridgs veth-red <--> veth-red-br and veth-blue <--> veth-blue-br
ip link add veth-red type veth peer name veth-red-br
ip link set veth-red netns red
ip link set veth-red-br master v-net-0
ip -n red addr add 192.168.15.1 dev veth-red
ip -n red link set veth-red up
ip link add veth-blue type veth peer name veth-blue-br
ip link set veth-blue netns blue
ip link set veth-blue-br master v-net-0
ip -n blue addr add 192.168.15.2 dev veth-blue
ip -n blue link set veth-blue up
Finnaly attribute an adress ip to the virtual switch
ip addr add 192.168.15.5/24 dev v-net-0
test network : ping 192.168.15.1
The schema resume all operations :
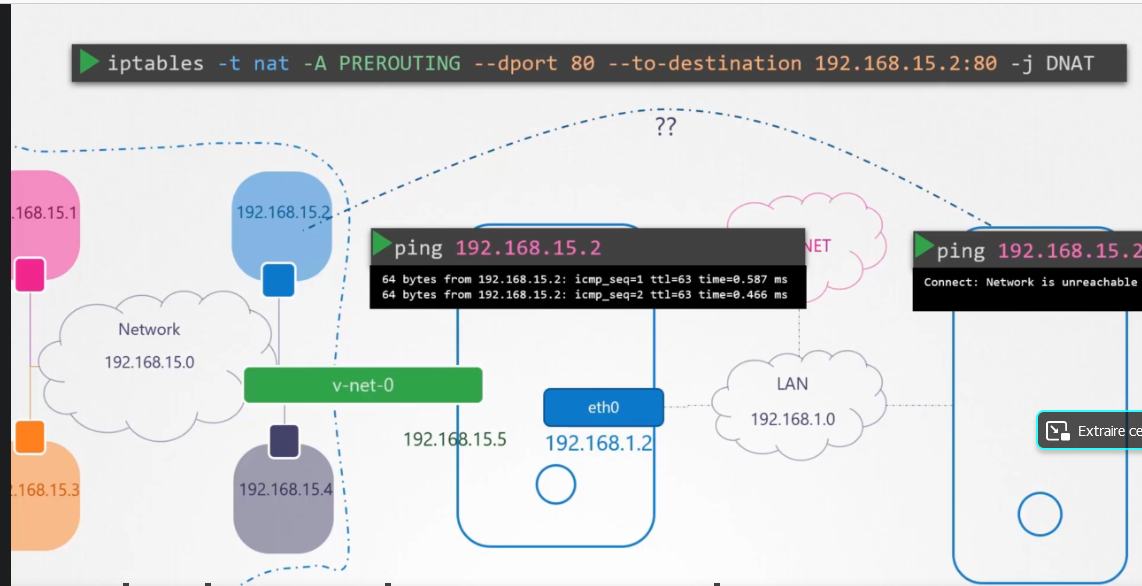
To connect with the other namespaces or networks , we should pass by a gateway:
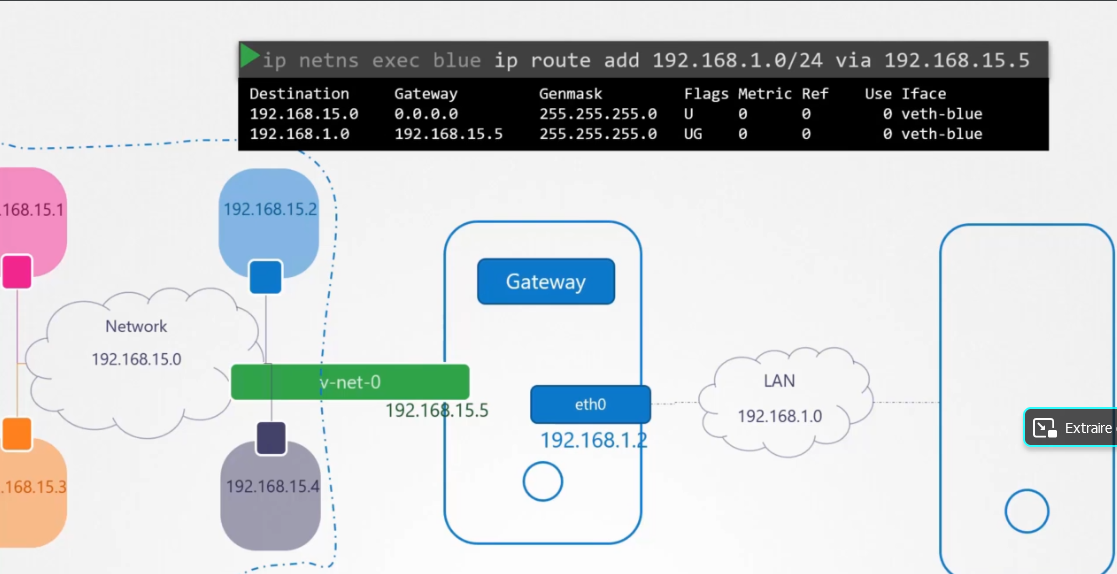
ip netns exec blue ip route add 192.168.1.0/24 via 192.168.15.5
but this it's not suffisant, we should NAT
Accepter les paquets retransmis via le périphérique d'IP interne du pare-feu permet aux noeuds du LAN de communiquer entre eux. Cependant, ils ne peuvent toujours pas communiquer vers l'extérieur (par exemple, vers l'internet). Pour permettre aux noeuds du LAN avec des adresses IP privées de communiquer avec les réseaux public externes, configurez le pare-feu pour le masquage d'IP, qui masque les requêtes provenant des noeuds du LAN avec l'adresse IP du périphérique externe du pare-feu (dans ce cas, eth0) :
iptables -t nat -A POSTROUTING -s 192.168.15.0/24 -j MASQUERADE
if the namespace should connect to internet
ip netns exec blue ip route add default via 192.168.15.5
if you nedd to connect other namespace with the namespace
iptables -t nat -A POSTROUTING -dport 80 --to-destination 192.168.15.2:80 -j DNAT
Core DNS
Core DNS is a server DNS in Kubernetes Cluster, to have more information, visit websites :
https://github.com/kubernetes/dns/blob/master/docs/specification.md https://coredns.io/plugins/kubernetes/
Cluster Networking
fdfdfd